









TTPay provides a seamless Web3 payment/payout solution with full support for USDT、USDC、ETH、BNB、TRX and major crytocurrencies payment , while aggregating Multi-chain crypto transactions including ETH, BNB, TRON, POLYGON, and more — all accessible through one API. With no KYC required, TTPay makes global payments easier, safer, and more efficient, helping you unlock new markets with instant conversion and acceptance of any cryptocurrency.
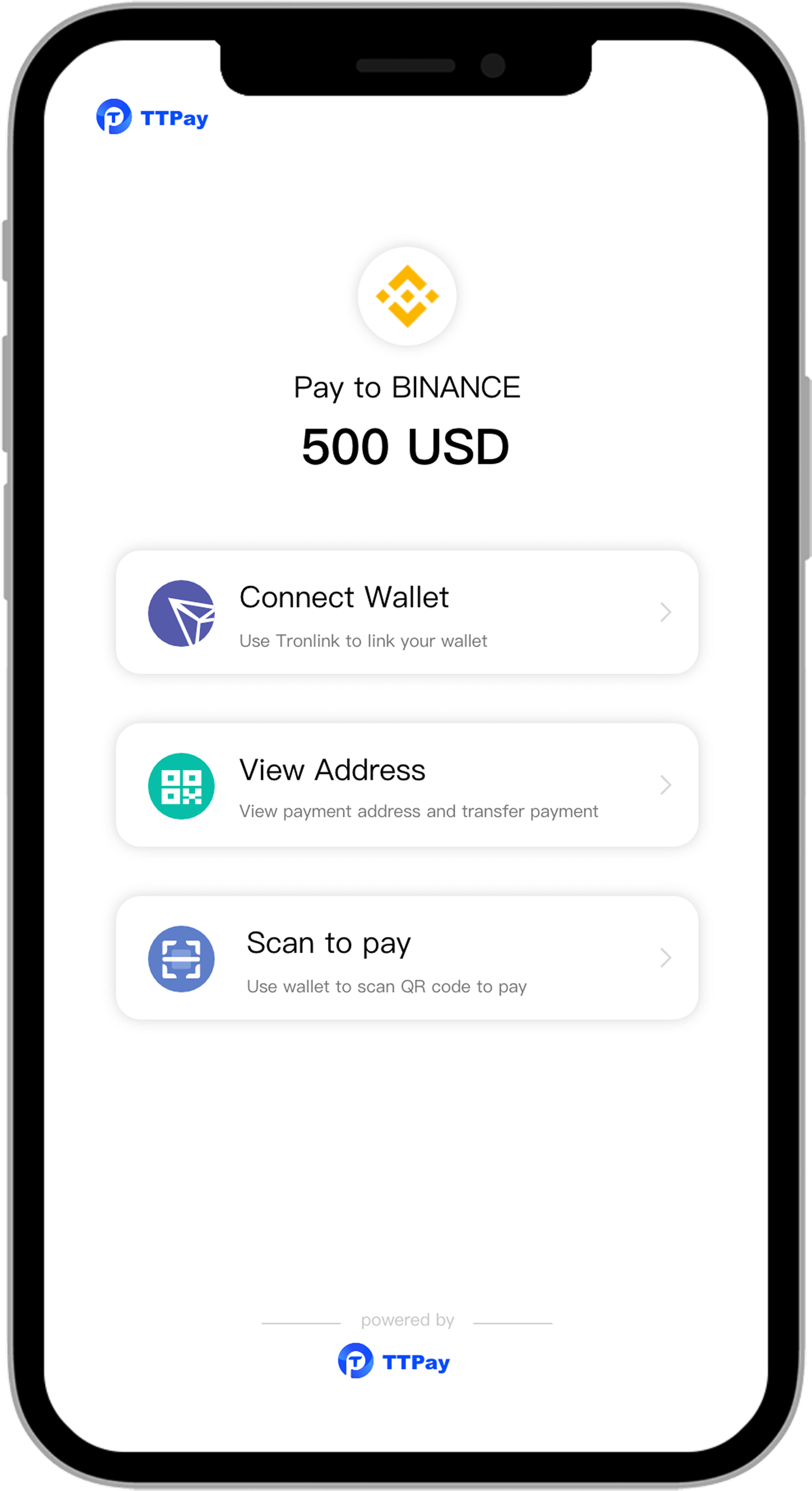
Designed for small-scale or personal USDT、USDC、ETH、BNB、TRX and major crytocurrencies payment collection, the platform automatically monitors transaction data, processes order confirmations without requiring API integration, and offers instant deployment with multi-chain compatibility
Merchants request the API to create an order, the platform automatically assigns the collection wallet and confirms the order after collection. There’s no need to provide the collection wallet. It supports multi-public chain multi-currency, payments from any mobile wallet, automatic fund pooling, cross-chain withdrawals, and a customized checkout page.
Web3-based system wallet white label services enable cryptocurrency payments on your website with no payment logo, without the need to jump through hoops for third-party payments, along with customized checkout page for branded merchants.
Merchants can send payouts to any wallet address with ultra-low fees, Supports multiple blockchains & cryptocurrencies, Real-time transfers with instant settlement, Flexible and fast integration
Designed for small-scale or personal USDT、USDC、ETH、BNB、TRX and major crytocurrencies payment collection, the platform automatically monitors transaction data, processes order confirmations without requiring API integration, and offers instant deployment with multi-chain compatibility
Merchants request the API to create an order, the platform automatically assigns the collection wallet and confirms the order after collection. There’s no need to provide the collection wallet. It supports multi-public chain multi-currency, payments from any mobile wallet, automatic fund pooling, cross-chain withdrawals, and a customized checkout page.
Web3-based system wallet white label services enable cryptocurrency payments on your website with no payment logo, without the need to jump through hoops for third-party payments, along with customized checkout page for branded merchants.
Merchants can send payouts to any wallet address with ultra-low fees, Supports multiple blockchains & cryptocurrencies, Real-time transfers with instant settlement, Flexible and fast integration











All-in-one crypto payment gateway for Web3, making global transactions simple and secure.
Anonymous Payment ensures no personal information is retained, offering secure encrypted transactions that cannot be traced, protecting the privacy of each user's transfer.
It is free to settle in, and we provide a powerful and customizable checkout page with Multi-chain support, enabling multi-currency and multi-wallet payments.
According to your needs, we provide a variety of payment methods, including USDT Payment,with handling fees as low as 0.8%.
With Web3 T+0 settlement, you can withdraw anytime and anywhere without waiting, perfectly solving the problem of transaction lag.


High commissions and stable settlement make your resources easier to monetize.
Customizable checkout, Telegram bot notifications, one-click payouts, automatic fund consolidation, cross-chain withdrawals, multi-currency & multi-chain reports, fast integration, and instant callbacks.
Start now